If you have to create an archive of past events, this scenario is for you. The main focus here is storage of event data. Potentially, data is stored for a long time and eventually never being overwritten. It is also highly likely that data will be written to a read-only media like CD-R.
Event archive are created for a number of reasons, some samples are
- Corporate requirementsYour organization, as a general policy, requires you to log data for later review.
- ISO 9000 requirementsDepending on where logs are being generated, they might be needed to be long-term archived to fulfil the ISO 9000 requirements.
- legal requirementsDepending on your country, some or all organizations might be required by law to save log data for an extended period of time. For example, in many countries internet service providers are required by law to archive connection logs for at least some month so that criminal investigators can use them to track down cyber-criminals.
Depending on the exact requirements you have, the event archive can be placed on a server that performs other functions or it can not. If the log archive is potentially used in court, we highly recommend to use a dedicated and specifically configured machine.
Creating an “unsecured” Event Archive
By “unsecured”, we mean an archive that is created without any specific measures against tampering with the log data. This type of archive is meant to be used for internal audits, only. This archive is not intended to be used as evidence in court. As such, a less restrictive security policy might be used.
This scenario is often found in organizations where event archiving is not the topmost priority and funding thus is limited. The advantage of an unsecured archive is that no dedicated machine or complex procedures are needed. If that level of security is sufficient for your application, the unsecured archive can be placed on event repository server that also performs other actions. For example, the event data could be written to a database which is also access by other tools.
However, as a general recommendation, we recommend to write archives as text files, which can later easily be compressed and written to read only media (if there is justification for this). This also allows to keep the database clean of otherwise unneeded historical data.
Setting up a unsecured event archive is relatively trivial.
- We recommend following the “Creating a simple Syslog Server” step-by-step guide.
- If you would like to receive Windows event log data or other non-syslog based events, we recommend to set up a SETP server and use SETP for relaying messages from the local Agents. This is described in “Forwarding NT Event Logs to a SETP Server”.
- Keep in mind that both the syslog server and the SETP server can run concurrently!
- Point all your log sources to the log host. Instructions for common syslog devices can be found in ““Sample Syslog Device Configurations”.
Creating a highly secure Event Archive
This type of archive is needed if log data is potentially to be used in court. Please note that some countries require organizations to store log data securely.
As law is very different in different countries and states, this guide here can not provide a definite answer on how to set up an archive to comply with local laws or to be used as evidence. You need to work with your legal advisor on how to do that. However, Adiscon’s scenario here describes some steps that are typically required.
A secure event archive is one where event data can not be tampered (or at least where it is highly unlikely). As such, special care must be taken that the system the archive resides on is tamper-resistant as well as the archived logs.
A typical configuration for a secure log host looks as follows:
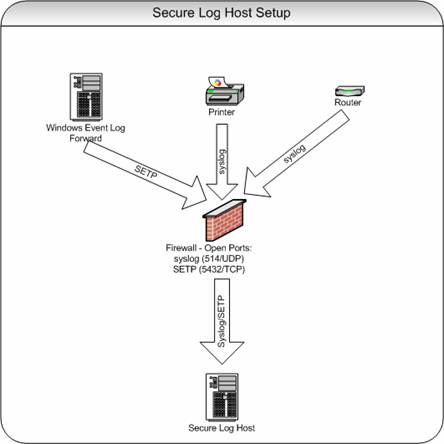
As a general guideline, we recommend the following steps to create a highly secure event archive:
- Firstly, check with your legal counsel and make sure you understand the legal requirements and implications of your doing! This is an essential step. If, for example, event log data is meant to be used in court and there is even a slight failure in your procedures, the data can not be used as evidence!
- Make sure that the central log host is a dedicated, well-equipped machine.
- Ensure physical security of the central log host.
- Ensure that the log host is protected by a firewall and there is no other system inside the log host’s network. Remember: nowadays firewalls have become quite inexpensive. If in doubt, look for a Cisco PIX 501, which offer very much for very little money!
- Review “Creating a hardened log host” for information on hardening your log host.After mastering the initial steps, creating the log host itself is quite simple:
- Then, follow the “Creating a simple Syslog Server” step-by-step guide.
- If you would like to receive Windows event log data or other non-syslog based events, we recommend to set up a SETP server and use SETP for relaying messages from the local Agents. This is described in “Forwarding NT Event Logs to a SETP Server”.
- Keep in mind that both the syslog server and the SETP server can run concurrently!
- Point all your log sources to the log host. Instructions for common syslog devices can be found in “Sample Syslog Device Configurations”.This concludes the creation of the log host.
- Ensure that log data is written to offline media on a regular basis. It is highly recommended to use read-only media like CD-R or DVD-R. Using rewriteable made might make the archive questionable in court. As does writing too infrequently to offline media. We recommend a daily schedule. Be sure to make backup copies from this media and store it on two physically different, secure places. Keep in mind that log data contains very sensitive information: make sure no unauthorized person has access to it. For example, it is not the best idea to send these CDs via postal mail or regular courier.
- After you have finally set up your system and documented all procedure, be sure to re-check with your legal counsel.
- Finally, remember that security is not a one-shot! Neither is law. Be sure to apply all hot-fixes to your server as they become available and change your procedures as need arises. Be sure to check with your legal counsel on a regular basis to ensure continued compliance with legal requirements.As you have seen, when creating a secure log host, there are many things beyond the scope of Adiscon’s software to consider. The small guidelines above are hopefully a good starting point. But it is strongly advised to check with other security sites (like www.cert.org) and consultants before implementing such a system. Your local government might even run a dedicated site with recommendations.
Creating a log archive for Evidence in Court
This is more or less the same scenario as “Creating a highly secure Event Archive”. We are providing a separate section as many people have inquired about some legal specifics. So we have tried to find some good sources, which we list here.
Again, we can not and do not provide legal advise here – check with your legal counsel before implementing any solution.
If you are based in the US, there are a number of government papers and sites available.
In the US, you might also want to visit www.cybercrime.gov.
To set up a log archive that should potentially be used as evidence in court, please read the chapter “Creating a highly secure Event Archive” of this post.